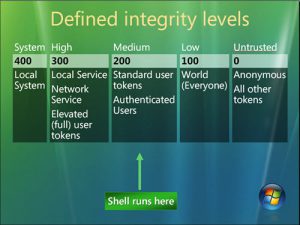
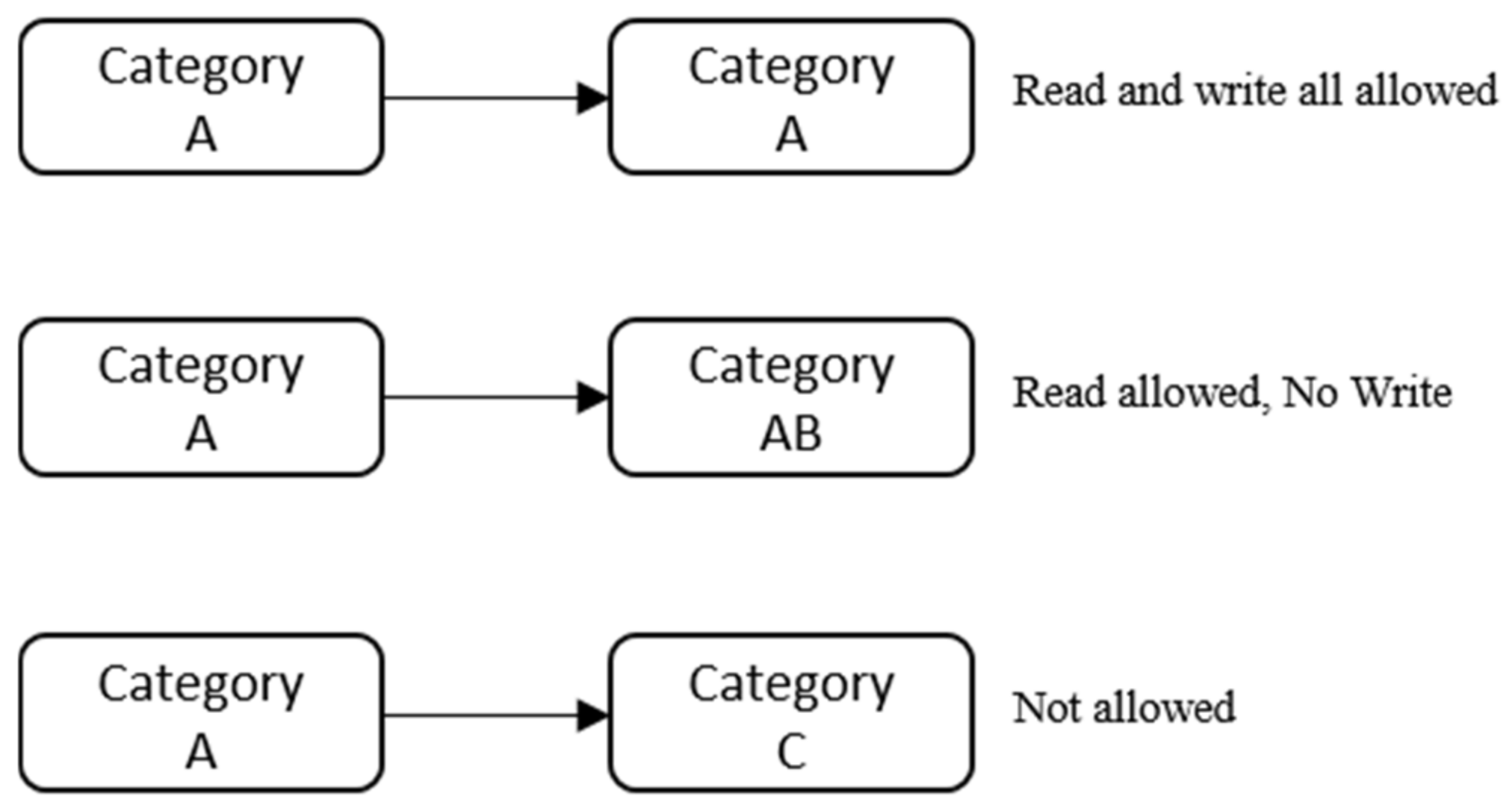
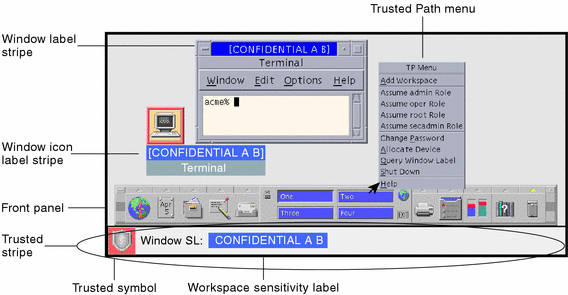
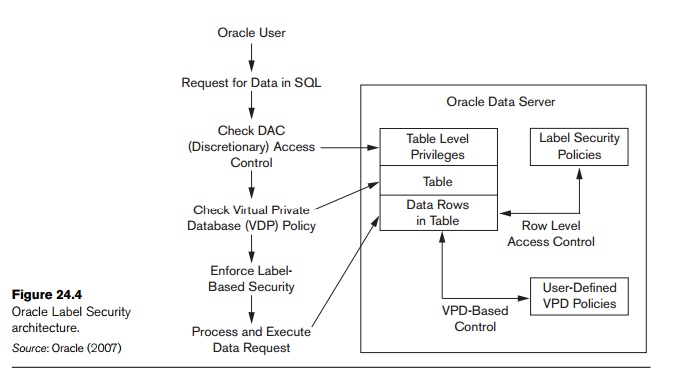
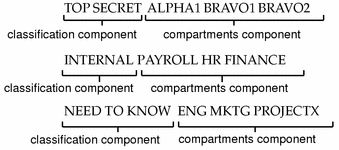
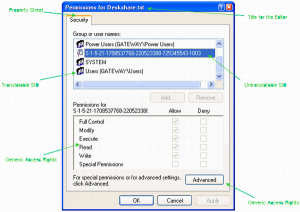
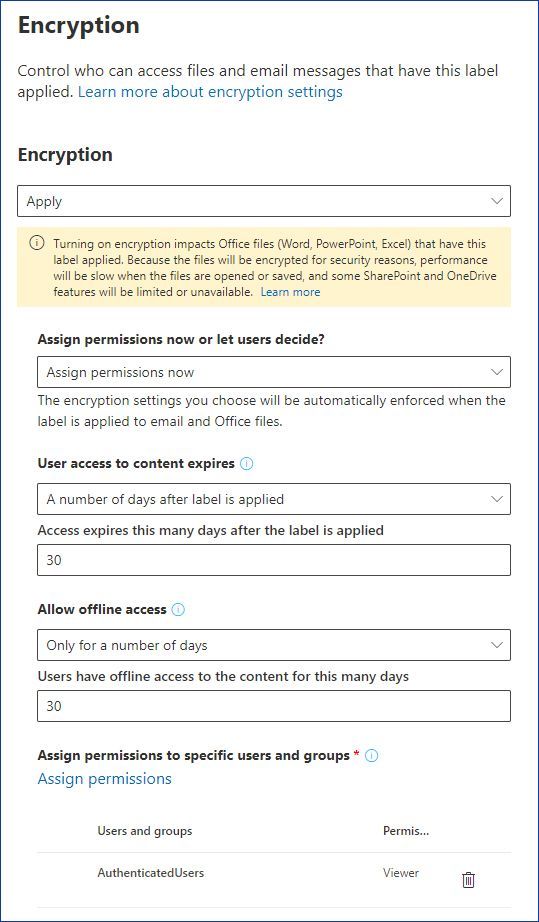
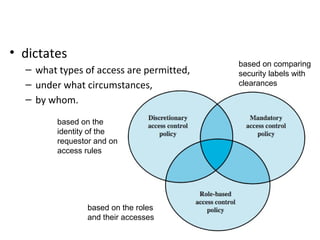
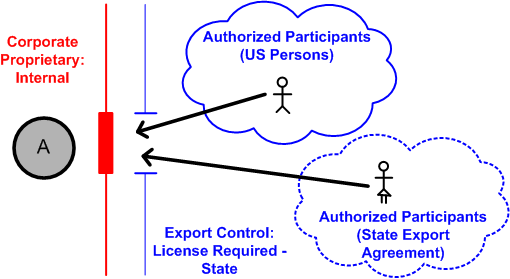
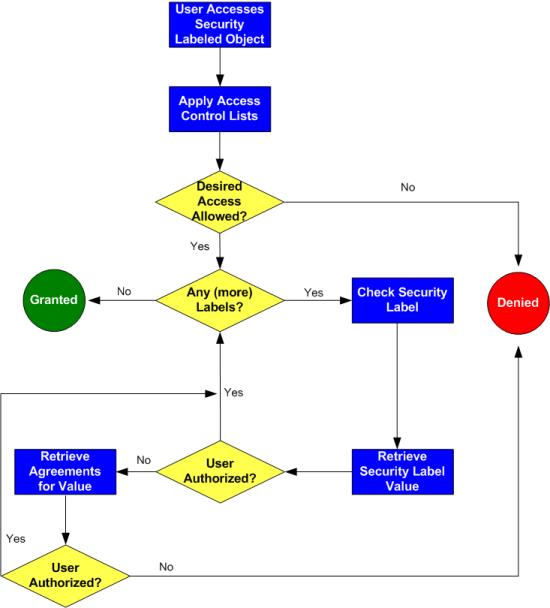
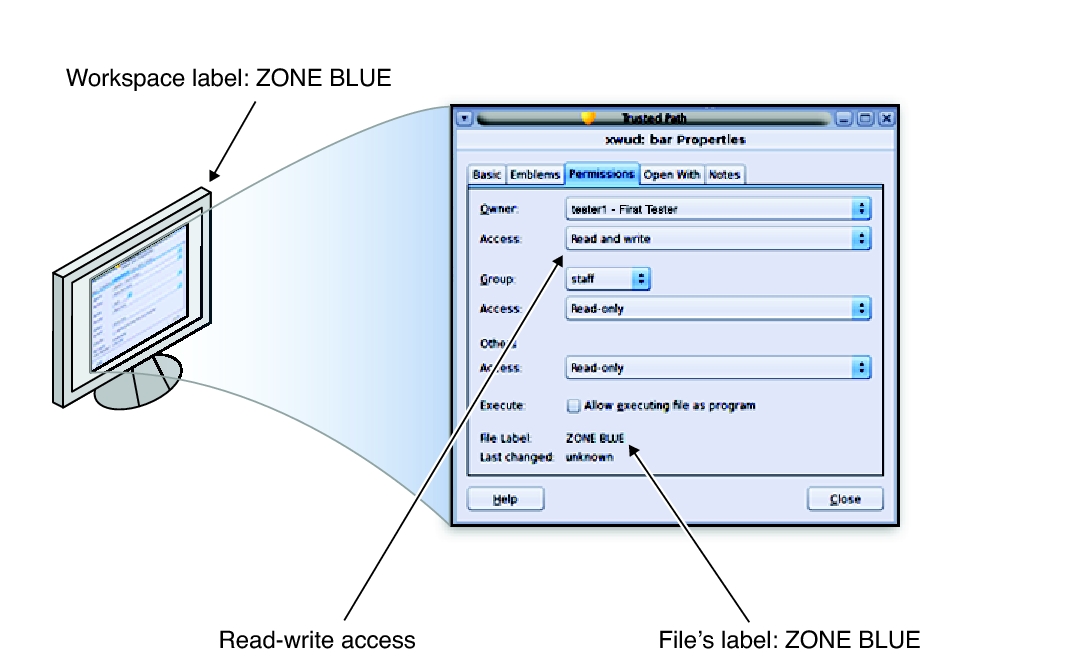
42 security labels access control
Products - Red Hat Customer Portal Red Hat 3scale API Management makes it easy to manage your APIs. Share, secure, distribute, control, and monetize your APIs on an infrastructure platform built for performance, customer control, and future growth. Gerrit Code Review - Access Controls - Google Open Source This security feature tries to prevent a role with Run As capability from modifying the access controls in All-Projects, however modification may still be possible if the impersonated user has permission to push or submit changes on refs/meta/config. Run As also blocks using most capabilities including Create User, Run Garbage Collection, etc ...
Access control with IAM | BigQuery | Google Cloud Oct 19, 2022 · 1 For any job you create, you automatically have the equivalent of the bigquery.jobs.get and bigquery.jobs.update permissions for that job.. BigQuery predefined IAM roles. The following table lists the predefined BigQuery IAM roles with a corresponding list of all the permissions each role includes.
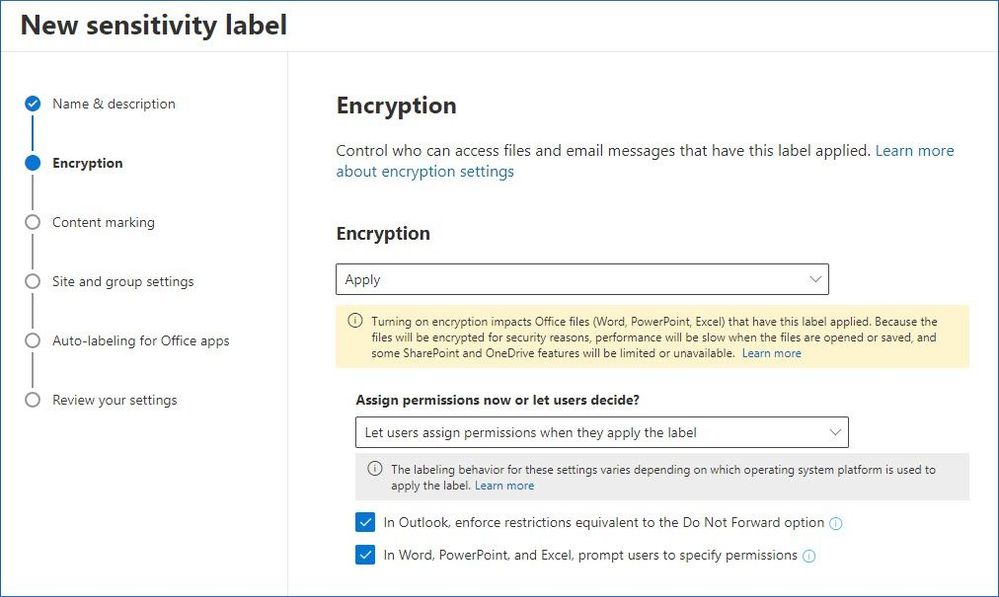
Security labels access control
Permissions - Security & Compliance Center - Office 365 Sep 27, 2022 · These people can perform only the tasks that you explicitly grant them access to. To access the Security & Compliance Center, users need to be a global administrator or a member of one or more Security & Compliance Center role groups. Permissions in the Security & Compliance Center are based on the role-based access control (RBAC) permissions ... Mandatory access control - Wikipedia Sun's Trusted Solaris uses a mandatory and system-enforced access control mechanism (MAC), where clearances and labels are used to enforce a security policy. However note that the capability to manage labels does not imply the kernel strength to operate in multilevel security mode [ citation needed ] . Access control - Wikipedia In the fields of physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process. The act of accessing may mean consuming, entering, or using.
Security labels access control. Computer access control - Wikipedia In computer security, general access control includes identification, authorization, authentication, access approval, and audit.A more narrow definition of access control would cover only access approval, whereby the system makes a decision to grant or reject an access request from an already authenticated subject, based on what the subject is authorized to access. Access control - Wikipedia In the fields of physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process. The act of accessing may mean consuming, entering, or using. Mandatory access control - Wikipedia Sun's Trusted Solaris uses a mandatory and system-enforced access control mechanism (MAC), where clearances and labels are used to enforce a security policy. However note that the capability to manage labels does not imply the kernel strength to operate in multilevel security mode [ citation needed ] . Permissions - Security & Compliance Center - Office 365 Sep 27, 2022 · These people can perform only the tasks that you explicitly grant them access to. To access the Security & Compliance Center, users need to be a global administrator or a member of one or more Security & Compliance Center role groups. Permissions in the Security & Compliance Center are based on the role-based access control (RBAC) permissions ...

Keychain Sticker Card Label Key IC Keychain Access Control EM Keychain Token Portal Reader 13.56MHZ RFID Multi-color Optional



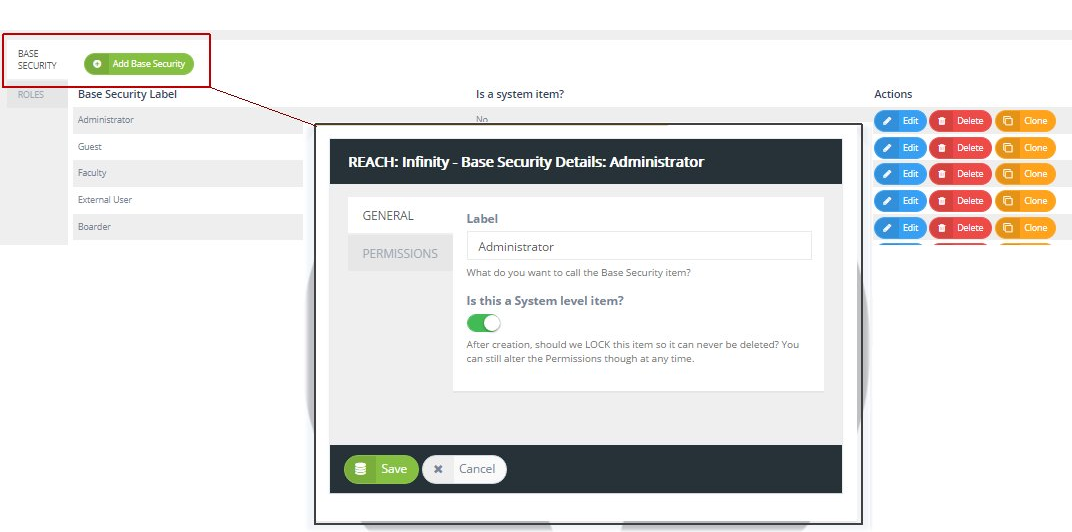
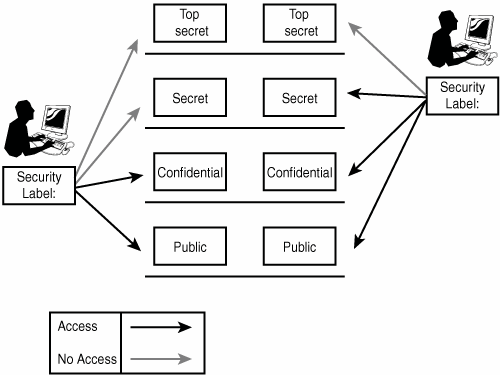
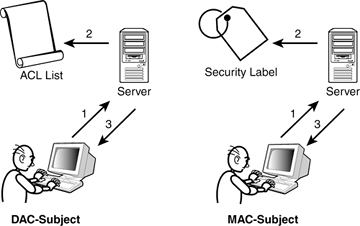
















Post a Comment for "42 security labels access control"